In our previous Blog you have understood what Authorization & Authentication are and how they are different from each other
In this Blog we would go through some of the famous Authorization & Authentication mechanisms which are used widely such as OAuth 2.0 and the OpenID Connect
OAuth 2.0 is the industry-standard protocol for authorization and not for authentication. It is used for providing access to resources such as API’s or any data which should not be accessible to any unknown user.
OAuth 2.0 focuses on client developer simplicity while providing specific authorization flows for web applications, desktop applications, mobile phones, and living room devices.
In Today’s blog we will be talking about the Authorization Code Grant type
We at MuleDreamin want to keep things simple & Interesting !
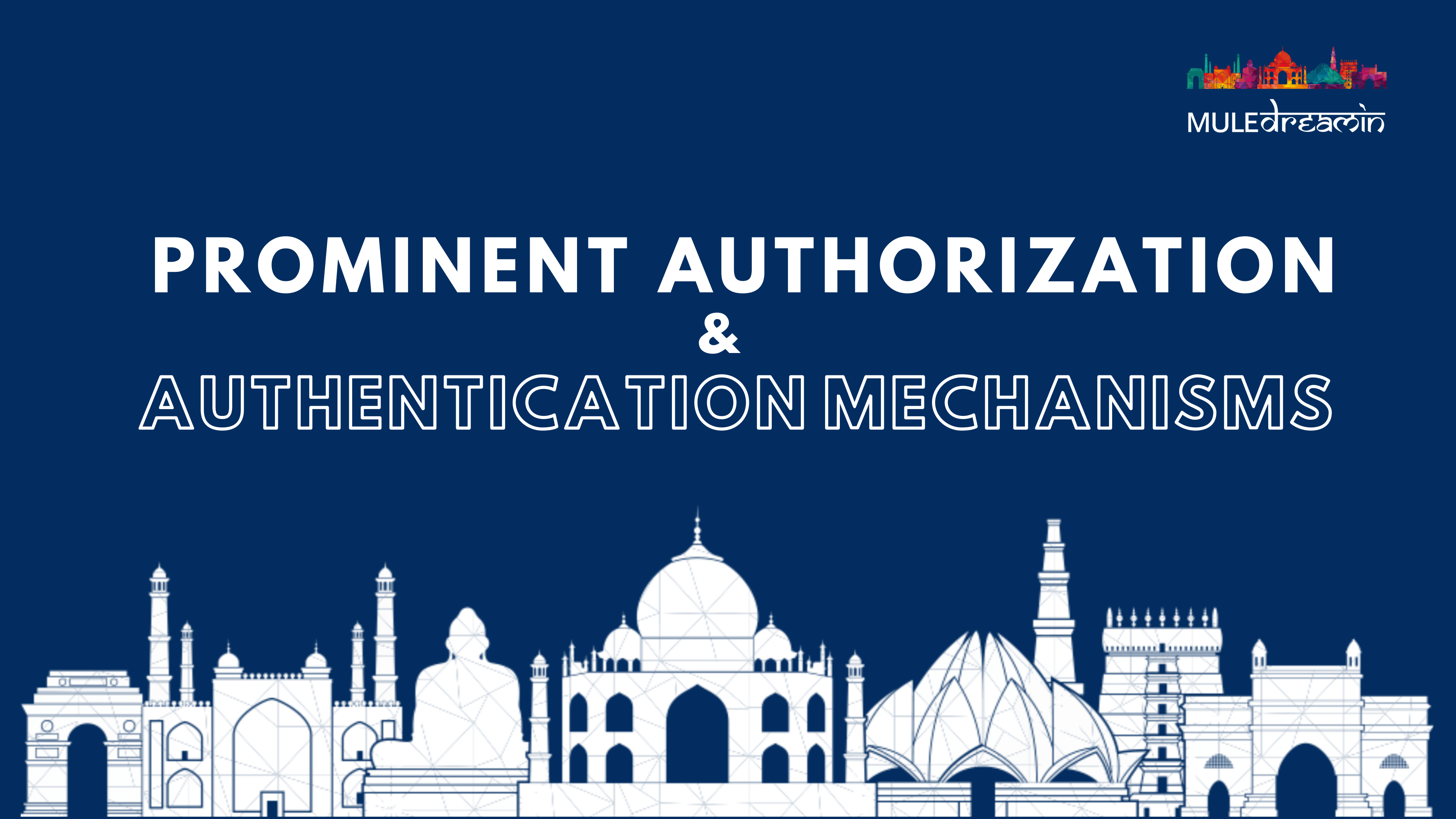
So let's begin with a scenario where you have a bank Account at MoneyMule Bank while you were happy with the services but some of the features like displaying adequate data or helpful data on the Dashboards were not present , you turned up to MuleDreamin Smart Manager Application. This application provides you detailed insights and is very helpful.
But How can MuleDreamin Smart Manager Application access your data present in MoneyMule Bank ?
Sharing your username and password with MuleDreamin Smart Manager Application to access your data on behalf of you is totally insecure as it was doing some transactions or activities which it should have been supposed to do !
You use OAuth 2.0 as the Authorization Framework so that the client application MuleDreamin Smart Manager Application can access your data in the MoneyMule Bank.
The Authorization Code grant type is used by web and mobile apps.
Before proceeding further, let’s have a look at some of the terminologies used in Oauth 2.0 :
Client: The client is the application that’s trying to access the user’s account. It needs to get permission from the user before accessing the account. In our case MuleDreamin Smart Manager Application is the client which wants to read your data present in the Money Mule Bank Resource Server
Authorization Server: The authorization server validates the user credentials and redirects the user back to the client with an authorization code which then the client sends back with some additional information to gain access token
Resource Owner: Resource Owner is you owns data in the Resource Server ( MoneyMule Bank)
Scope: It specifies the level of access that the application is requesting from the client.
Resource Server: Contains the resource owners data and sends out the requested data in response to any request made provided if access is valid.
At first the MuleDreamin Smart Manager Application should have registered with MoneyMule
Bank by doing this the bank would return MuleDream SMA.
i) ClientId
ii) Client Secret
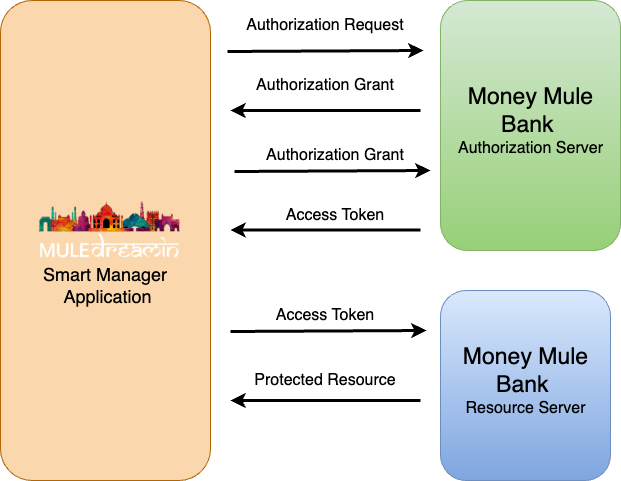
At High Level the OAuth 2.0 for grant type Authorization code
i) The application opens a browser to send the user to the OAuth server
ii) The user sees the authorization prompt and approves the app’s request
iii) The user is redirected back to the application with an authorization code in the
query parameters
iv) The application exchanges the authorization code for an access token
v) The application will now use this access token to request and access the protected
resources such as data.
Read more about Oauth 2.0 Authorization Code Grant
Oauth 2.0 is mainly used for Authorization Now we will learn about OpenId Connect which is used for authentication and built on top of OAuth 2.0 .
OpenID Connect is an OpenID Foundation (OIDF) standard that leverage OAuth 2.0 flow to add an identity layer in order to obtain basic information of the end user to verify the identity of the user on the basis of the authentication done by an Authorization Server or Identity Provider (IDP).

Open ID Connect is primarily used for Single Sign On ( SSO ) which means instead of creating your username and password for each application you can use the identity present in an application to login in different applications e.g. You can use Your login into an application using your Facebook’s identity as simple as that !
Since OIDC is built on top of OAuth 2.0 some of the vital terminologies such as Client Authorization Server etc are the same but apart this there is one more parameter that helps the client identify the user which is an ID Token.
An Id Token is different from the access token while an access token authorizes the client to access resources owned by you from the resource server the ID token is used to identify the resource owner..
It is this ID token which is also known as the JSON Web Token (JWT), which contains claims, claims containing statements like an email address or name of the user and some additional metadata.
Coming back to the scenario where you as a resource owner has granted MuleDreamin Smart Manager Application to access your data in MoneyMule Bank but to login into MuleDreamin Smart Manager Application you need to use your Google’s Id.
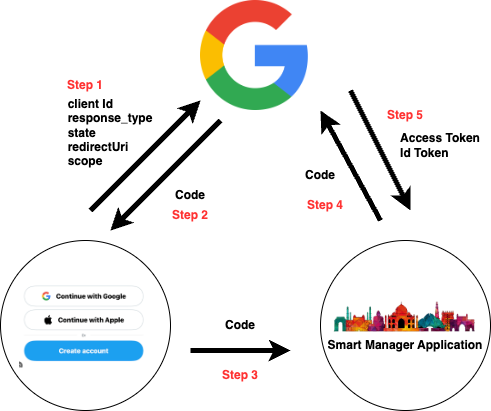
Step 1: User navigates to the MuleDreamin Smart Manager Application , clicks on the Sign in option , the user is then navigated to a google sign page where the user selects their google account and subsequently passes a parameters like scope, response_type , client_id, redirect_uri and state.
Step 2: The OpenID provider in our case Google authenticates the user that is you for a particular application instance.
Step 3: A one-time-use code is passed back to the client using a predefined Redirect URI.
Step 4: The user interface then shares this temporary code with the server inorder to open the ID token.
Step 5: The server can exchange this code to obtain ID token in order to get access to the user’s profile.